Data breaches can seriously harm businesses, leaking customer information, financial details, and other sensitive data. When such incidents occur, the effects can range from financial losses to severe damage to a business’s reputation.
It’s essential for businesses to act quickly and effectively in responding to a breach to reduce these negative impacts. A well-planned response can help control the situation, safeguard affected data, and assist in the recovery process, helping to maintain trust with customers and partners.
In this article, we discuss the crucial aspects of dealing with data breaches, including understanding what data breaches are and their implications, the immediate steps necessary for an effective response and the data recovery process. Also, we explore how professional data recovery software like Stellar can be helpful in retrieving lost data, ensuring businesses can resume operations swiftly and securely.
Understanding Data Breaches

A data breach occurs when unauthorized individuals gain access to private and confidential information. This can happen through various means and often leads to the release of sensitive data such as personal identification details, credit card numbers, or proprietary business information.
Common Types of Data Breaches:
- Hacking: Attackers exploit security weaknesses in software or networks to access protected data.
- Phishing: Through deceptive emails or messages, attackers trick individuals into providing sensitive information or accessing malicious websites.
- Insider Threats: Sometimes, employees or contractors misuse their access to steal or leak information.
Data breaches can have severe consequences for businesses, both immediately and over the long term. In the short term, companies often experience operational disruptions and financial losses, which include not only the theft of resources but also the expenses related to addressing the breach.
Over the long term, the repercussions of a data breach can extend to eroded customer trust and a subsequent loss of sales. Additionally, there may be ongoing legal consequences as businesses face compliance issues with privacy laws and regulations, further impacting their operations and reputation.
Immediate Response to a Data Breach
When a data breach occurs, a swift and decisive response is essential to manage the situation. This section covers the initial steps a business should take immediately after discovering a breach.
Detection and Identification:
- Monitor Systems: Regularly check security tools and software alerts that can indicate unauthorized access.
- Verify the Breach: Confirm the breach by identifying unusual activity or data discrepancies. Engage IT professionals to trace the origin and method of the breach.
Containment:
- Isolate Affected Systems: Disconnect affected devices from the internet and the rest of the network to prevent the spread of the breach.
- Secure Physical Areas: Restrict access to sensitive areas to ensure no unauthorized physical access to hardware and data storage.
- Maintain Logs: Preserve existing logs and data before they are overwritten to aid in subsequent investigations.
Assessment:
- Determine the Data Affected: Identify what types of data were compromised, including customer, employee, or company confidential data.
- Scope of the Breach: Evaluate how widespread the breach is within the organization to understand the extent of the impact.
Taking these steps can help mitigate the effects of a data breach and provide a foundation for recovery and response efforts to follow.
See also: 9 Tips for Protecting Your Company and Consumer Data
Data Recovery Process
After a data breach, recovering the affected data is a key step in restoring business operations and maintaining trust. Businesses can employ several strategies to recover compromised or lost data.
One effective method is data restoration from backups, where recent backups are used to restore data that was affected during the breach. Additionally, forensic recovery techniques can be applied to retrieve data that may still be salvageable from damaged or compromised files.
In cases where data has been encrypted by ransomware, it is crucial to use decryption keys if they are available, or to seek assistance from cybersecurity experts who can aid in decrypting the affected data.
Another vital component in the data recovery process involves the use of specialized recovery tools. Software like Stellar plays a significant role in helping businesses efficiently recover lost data. Stellar and similar tools are equipped to restore a variety of data types, including files, folders, documents, emails, and other critical business data, from different storage mediums such as hard drives, SSDs, and RAID configurations.
These tools are particularly valuable for their ability to handle complex recovery tasks and their capability to work with various data loss scenarios. Additionally, resolving data discrepancies with enterprise search can streamline the process, ensuring that recovered data is accurate and consistent with the original records.
Critical Part of Data Recovery
The critical part of data recovery involves prioritizing the recovery of sensitive data like personal identifiable information (PII) and financial records. This helps prevent further misuse and aids in quicker business normalization.
Next, ensure that the recovery process is secure to avoid any additional breaches of sensitive data. After recovery, check the integrity of the data to ensure it is complete and unaltered from its original state. Additionally, conduct thorough audits to confirm that all critical data has been successfully recovered and is accurate.
By following these steps, businesses can tackle the complex process of data recovery with a structured approach, ensuring that essential data is prioritized and securely restored.
Using Stellar for Data Recovery
Stellar Data Recovery is a software tool designed to assist businesses in retrieving lost or compromised data. This capability is particularly valuable in the event of data breaches, where quick recovery is essential to minimize operational disruption and financial losses.
Stellar stands out due to its robust features that support recovery efforts following a breach. Notably, the software is equipped to handle complex recovery scenarios, including the retrieval of data from encrypted drives. This is a common challenge in cases of ransomware attacks, where data is locked by malicious software and made inaccessible without a decryption key.
Additionally, Stellar supports a wide range of file types and storage devices. It can recover documents, emails, photos, and other critical business data from hard drives, SSDs, USBs, and memory cards. Its versatility makes it a comprehensive tool for businesses looking to restore their operations swiftly after a data breach.
Stellar’s user-friendly interface also ensures that businesses can conduct recovery tasks with minimal technical expertise, making it accessible for non-specialist staff.
Step-by-Step Guide to Using Stellar Data Recovery Software
Using Stellar Data Recovery software involves a few straightforward steps that can greatly assist in the efficient recovery of lost or compromised data. Here’s a detailed guide on how to use Stellar effectively:
Step 1: Begin by launching Stellar and navigating its user-friendly interface. You’ll be presented with options to select the types of files you wish to recover—whether they are documents, emails, photos, or other types.
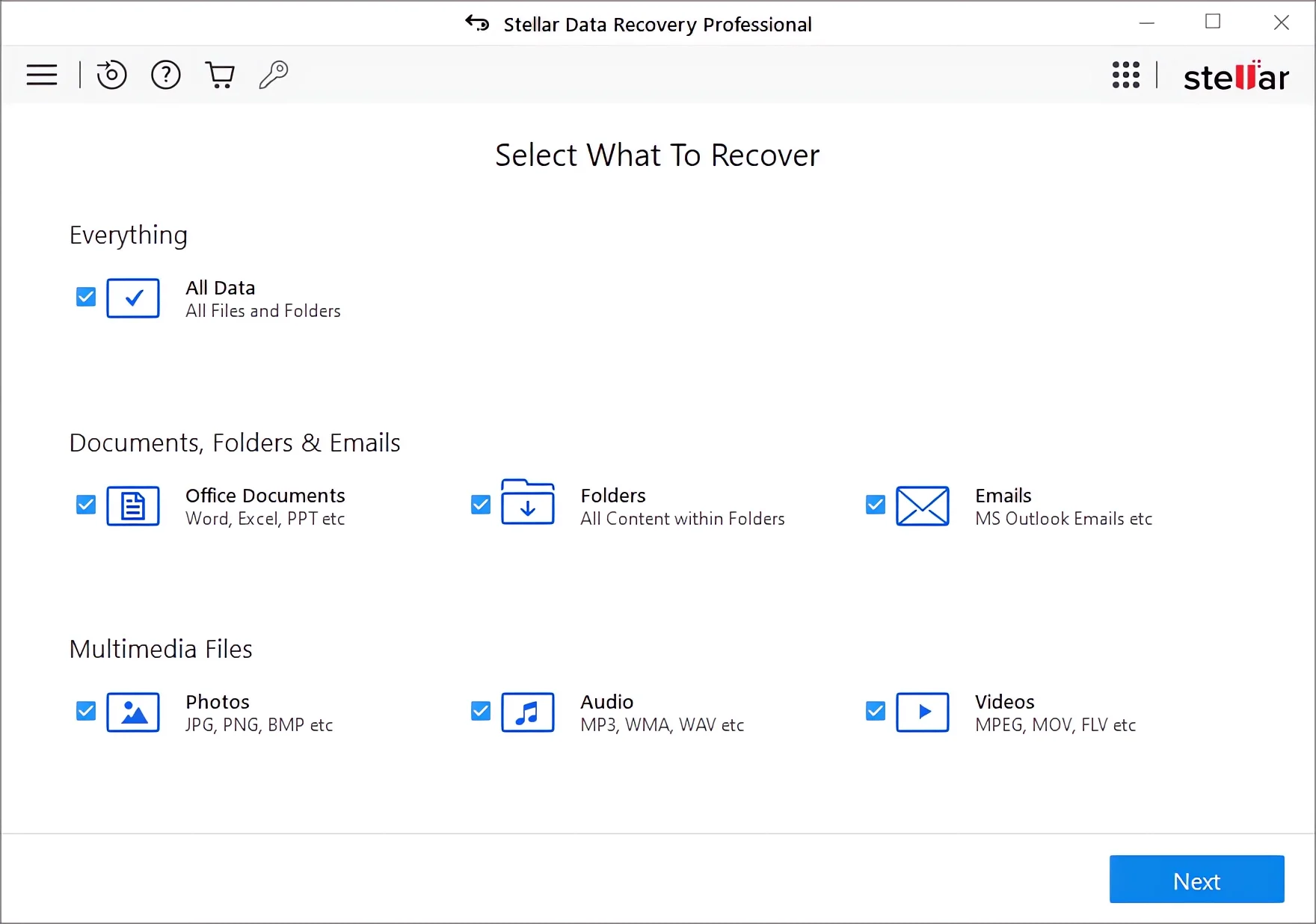
Carefully choosing the correct types of data you need to recover is essential. This focus helps streamline the scanning process, ensuring the software searches only for relevant data types, which can reduce the recovery time and increase the effectiveness of the scan.
Step 2: After selecting the data types, the next step is to specify where Stellar should look. You can select either a specific folder, an entire drive, or a volume to scan.
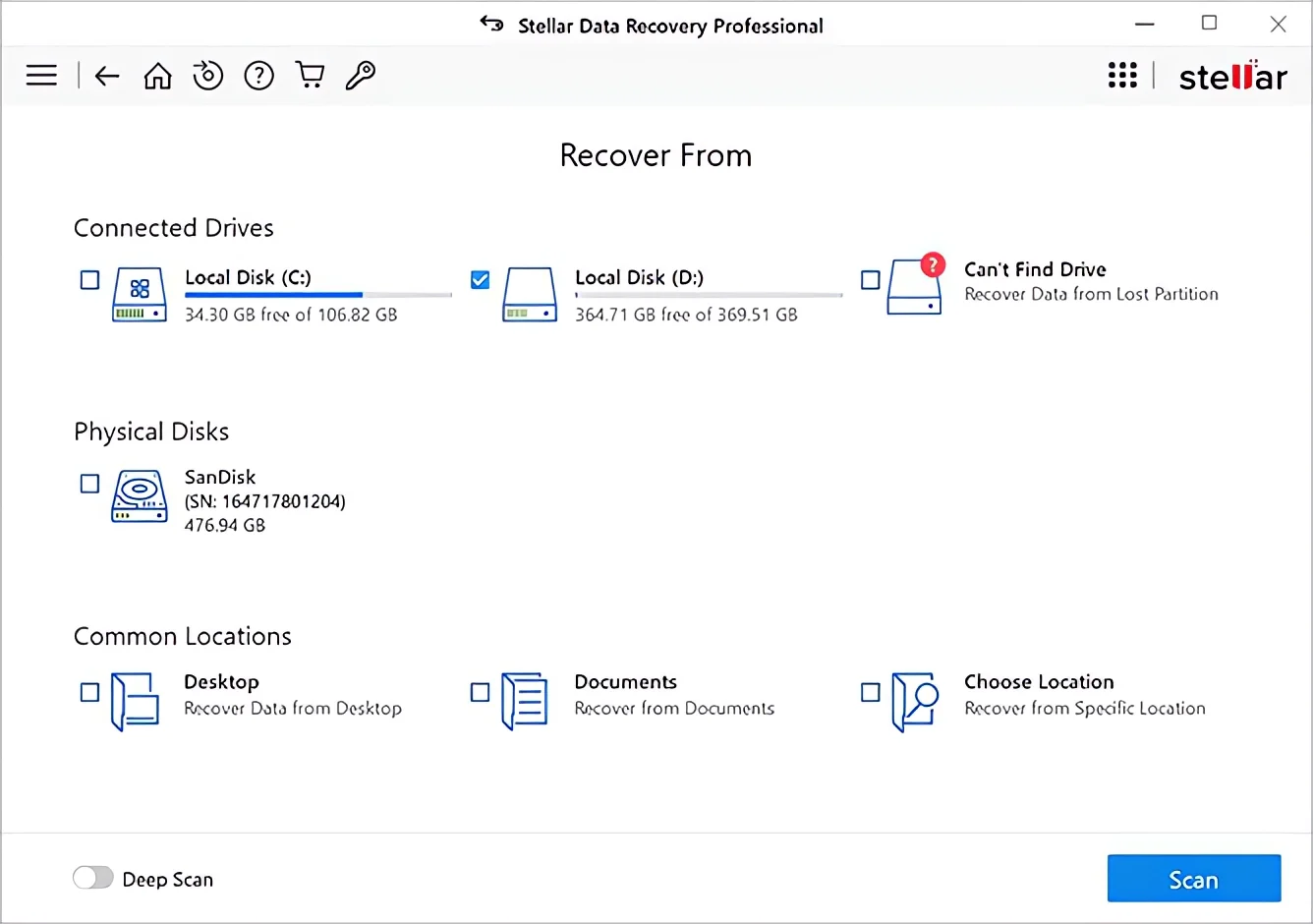
Click ‘Scan’ to start the process. Stellar will then proceed to thoroughly scan the selected location for recoverable files. The software uses advanced algorithms to search through the storage space, ensuring that even files that are not immediately apparent are detected.
Step 3: Once the scan completes, Stellar allows you to preview the recoverable files. This feature is particularly useful for ensuring that the files you are about to recover are the ones you actually need.
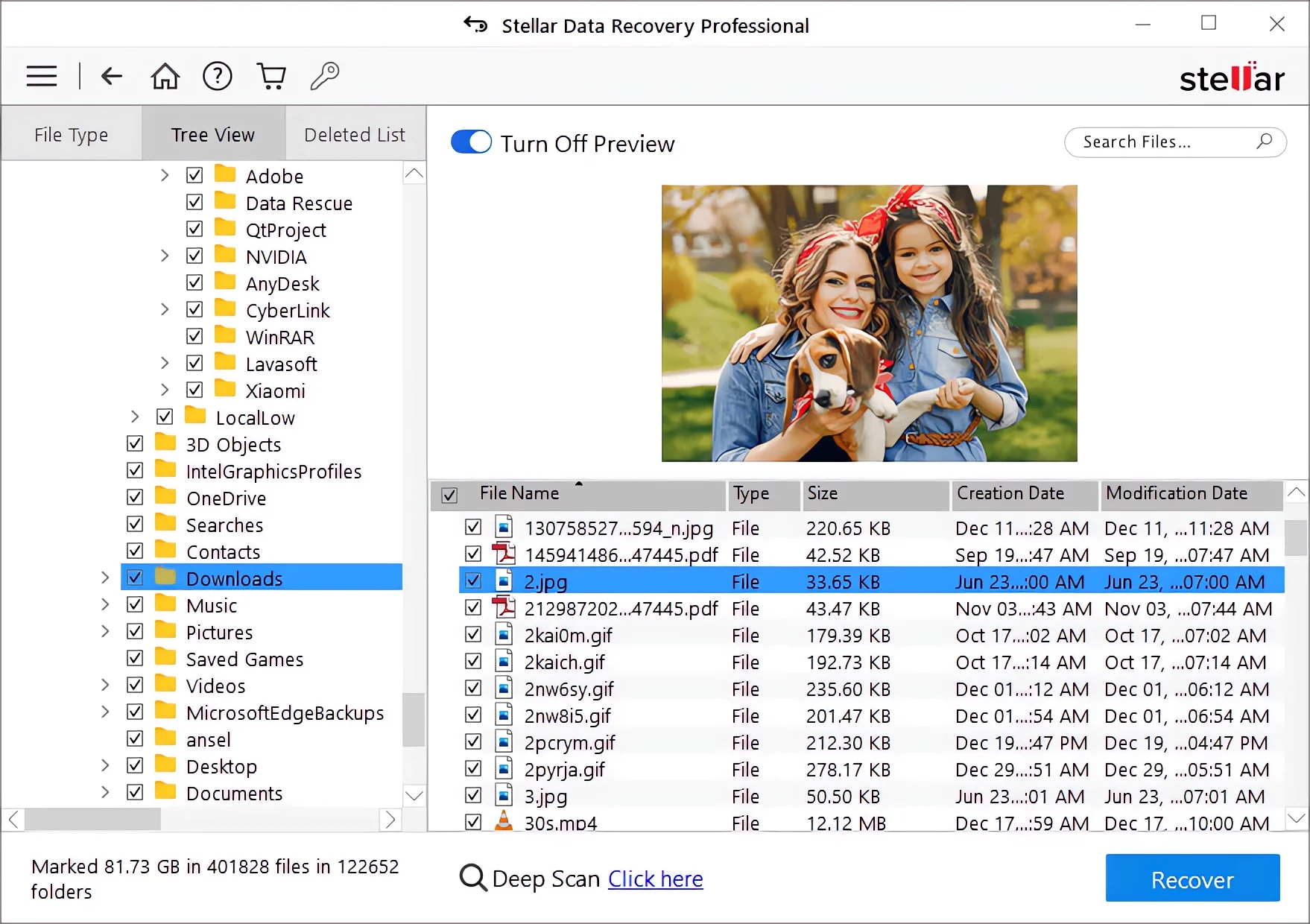
You can select individual files or entire batches for recovery. It’s important to check the files for completeness and relevance before final recovery.
Choose a secure location on another drive to save the recovered data. It’s recommended to save the data to a different device than the one it was recovered from to prevent any potential overwrite issues and to preserve the integrity of the data.
This process not only helps in bringing back lost files but also ensures that they are recovered securely and efficiently, reducing the potential stress and impact of data loss on your business.
Conclusion
Recovering from a data breach requires a prompt response to detect, identify, and isolate the breach, followed by a thorough assessment of the damage. Making use of data recovery tools is important for restoring lost or compromised data, particularly when dealing with encrypted drives.
Following the recovery phase, it is important to review and validate the integrity and completeness of the data before resuming normal business operations.
To minimize the need for data recovery in the future, businesses should adopt robust data management practices. This includes maintaining regular and secure backups of all critical data, implementing continuous monitoring systems to quickly detect unusual activities, and educating staff on data security best practices and phishing prevention.
Related Articles:
- How to recover lost password of Memory Card (MMC, micro SD)
- Revive Memories with Free SD Card and Disk Video Recovery Solutions
- Read this before you Surrender your Phone to Phone Repair Shops
- Why Partitioning Your Hard Drive Is a Smart Move for Your Data
- 7 Key Strategies to Prevent Data Loss in Your Organization
- 4 Ethical Consideration in Cloud Data Protection
- Preventing Data Loss: The Role of Secure FTP
- Understanding and Protecting Your Data Online
- Salesforce Data Management: Securing Your Business in the Cloud
